Latitude Group Holdings: Hack-Attack
On the morning of the 16 March, Aussie consumer finance play Latitude Group Holdings (LFS AU) announced what appeared to be a "sophisticated and malicious cyber-attack."
Shares were voluntarily suspended on the 20 March and were reinstated on the 22 March.
Latitude believes no compromised data has left its systems; but its review has uncovered evidence of large-scale information theft affecting customers (past and present) across Australia and New Zealand.
This stock is an avoid.
Despite its market cap, Latitude is illiquid. Look away now if this is not your bag.
On Latitude
Latitude is a digital payments, installments, and lending business that "helps businesses grow and people shop and finance their lives".
As at December 2022, Latitude had 2.8 million customer accounts and more than 5,500 merchant partners in Australia and New Zealand, and 5,800 accredited brokers throughout Australia.
Merchant partners include Harvey Norman, Urban Republic, and David Jones (which signed a credit card supply earlier this year).
Latitude IPOed on the 20 April 2021 at A$2.60/share. Here is the prospectus.
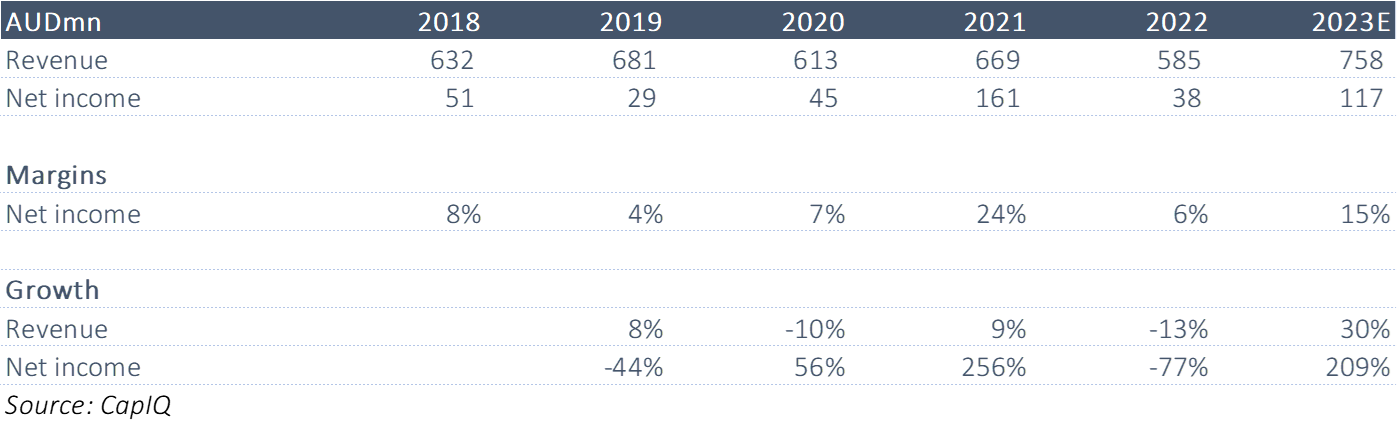
Recent results. FY22 (Dec Y/E) statutory NPAT of $57.9mnn from continuing operations.
Cash NPAT of $153.5mn, down 23% yoy.
Volumes was $7.95bn, up 8%.
2H22 dividend of 4 cents per share fully franked, took the full-year dividend to A$0.1185/share fully franked, versus A$0.157 (50% franked) in FY21.
Abridged Earnings
Shareholder Register
KKR held 100% prior to listing.
Shinsei entered into an S&P with KKR ahead of the IPO.
Shinsei/SBI lifted its stake to 14.97% on the 22 December 2022.
The Attack
On the 16 March, Latitude said:
that approximately 103,000 identification documents, more than 97% of which are copies of drivers’ licences, were stolen from the first service provider. Approximately 225,000 customer records were also stolen from the second service provider.
On the 20 March, Latitude announced:
approximately 330,000 customers and applicants have had their personal information stolen; approximately 96% of the personal information stolen was copies of drivers’ licences or driver licence numbers; less than 4% was copies of passports or passport numbers; and less than 1% was Medicare numbers.
On the 22 March, Latitude said:
to the best of our knowledge no compromised data has left Latitude’s systems since Thursday 16 March 2023, regrettably our review has uncovered further evidence of large-scale information theft affecting customers (past and present) and applicants across Australia and New Zealand.
Latitude said it working with the Australian Cyber Security Centre, and has alerted relevant law enforcement agencies and engaged several cyber security specialists.
The attack is now the subject of an investigation by the Australian Federal Police.
As the attack remains active, Latitude has taken its platforms offline and is unable to service its customers and merchant partners.
Restoration of these services is aligned to the forensic review.
Takeaways
The hack is the latest in cyber attacks to target corporates in Australia in recent months.
Intellectual property services provider IPH Ltd (IPH AU) reported on the 16 March it had detected unauthorised access to a portion of its IT environment.
Medibank announced on the 13 October it had detected unusual activity on its network, and later confirmed criminal access to 9.8mn Medibank current and former customers' personal data.
According to the SMH, Medibank said the cost of the cyberattack topped $26mn for the December half-year and is expected to be as much as $45mn for the full year.
This only covers the costs of dealing directly with the incident and not the additional costs of the investor lawsuits and regulatory action.
On the 22 September last year, Optus revealed about 10mn customers - about 40% of the population - had personal data stolen in a cyber-attack.
How much will this breach set back Latitude? Based on the estimated cost of the Medibank breach, some Street estimates place a number of $10mn to $15mn in costs associated with the mitigation of the incident.
These figures are speculative at best. It is early days since the attack was noticed.
I don't think the final cost should simply be a matter of comparing Medicare's cost and customers affected and applying across to Latitude.
Latitude, as a financial services business, should have higher security standards.
Latitude's market cap is down A$42mn since the announcement.
Latitude has also notified its insurers of the incident. I'd be curious to understand how much insurers will backstop costs incurred.
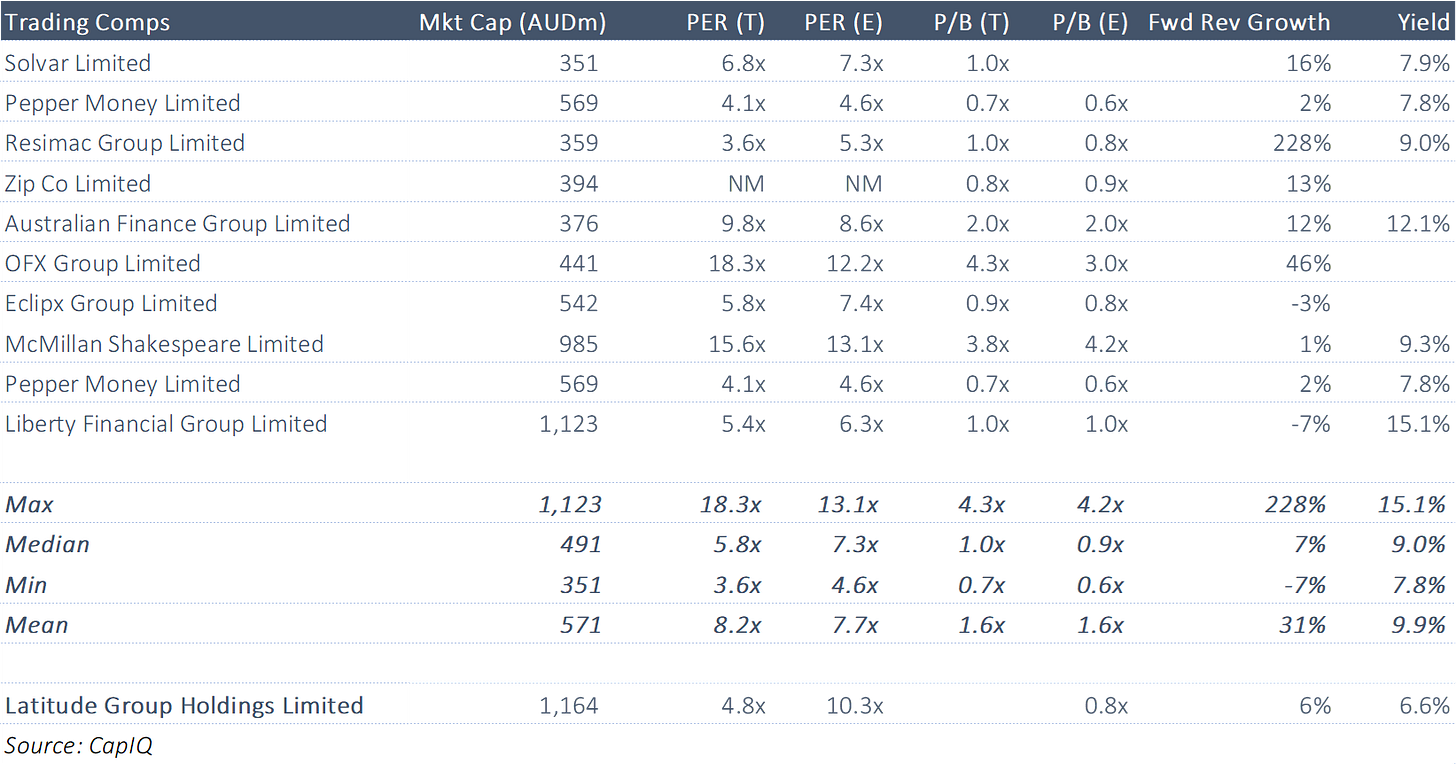
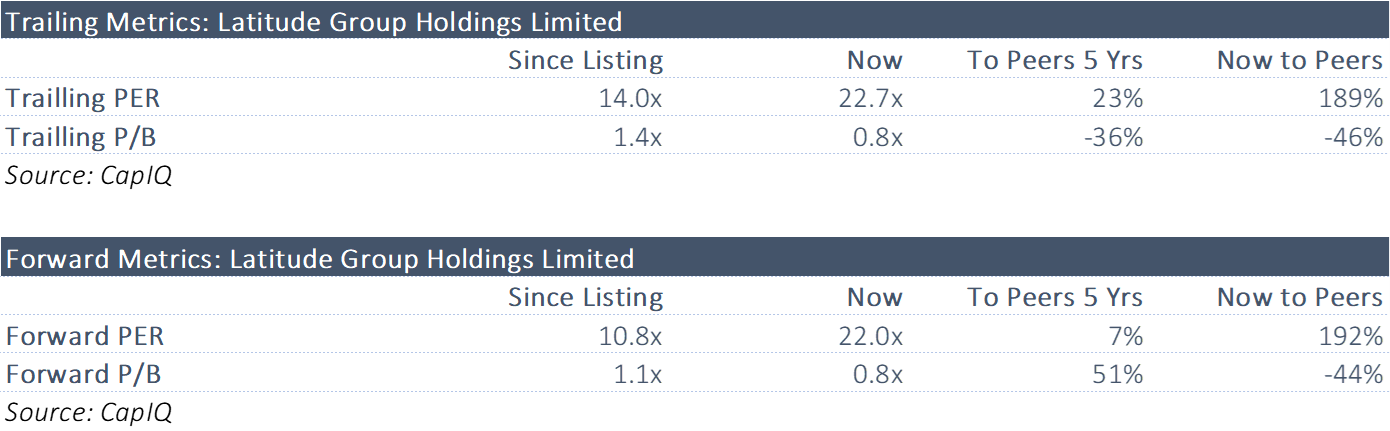
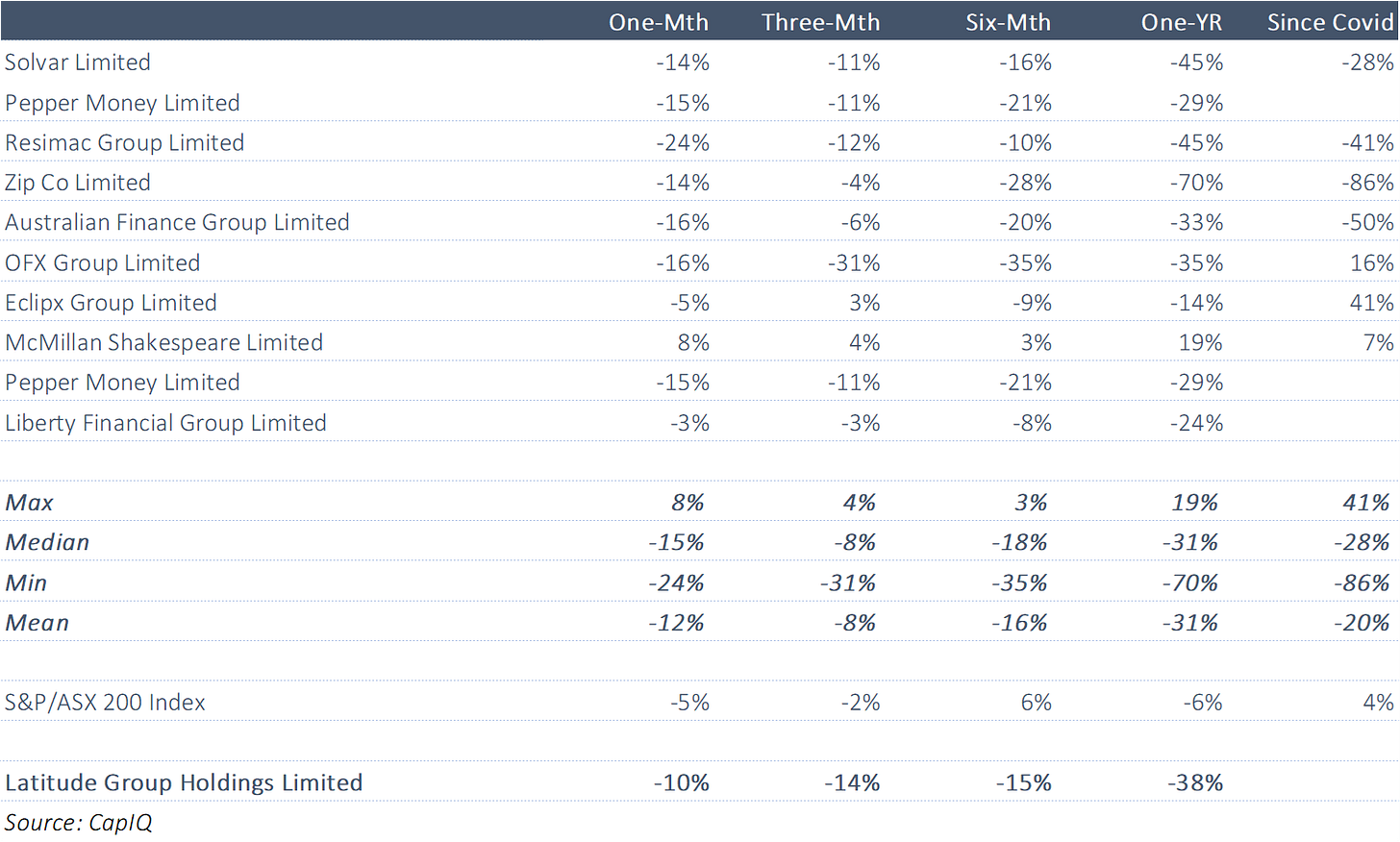
Versus Peers
Multiples for Latitude do not appear overly expensive here.
Latitude's forward multiple is roughly in line with that since listing.
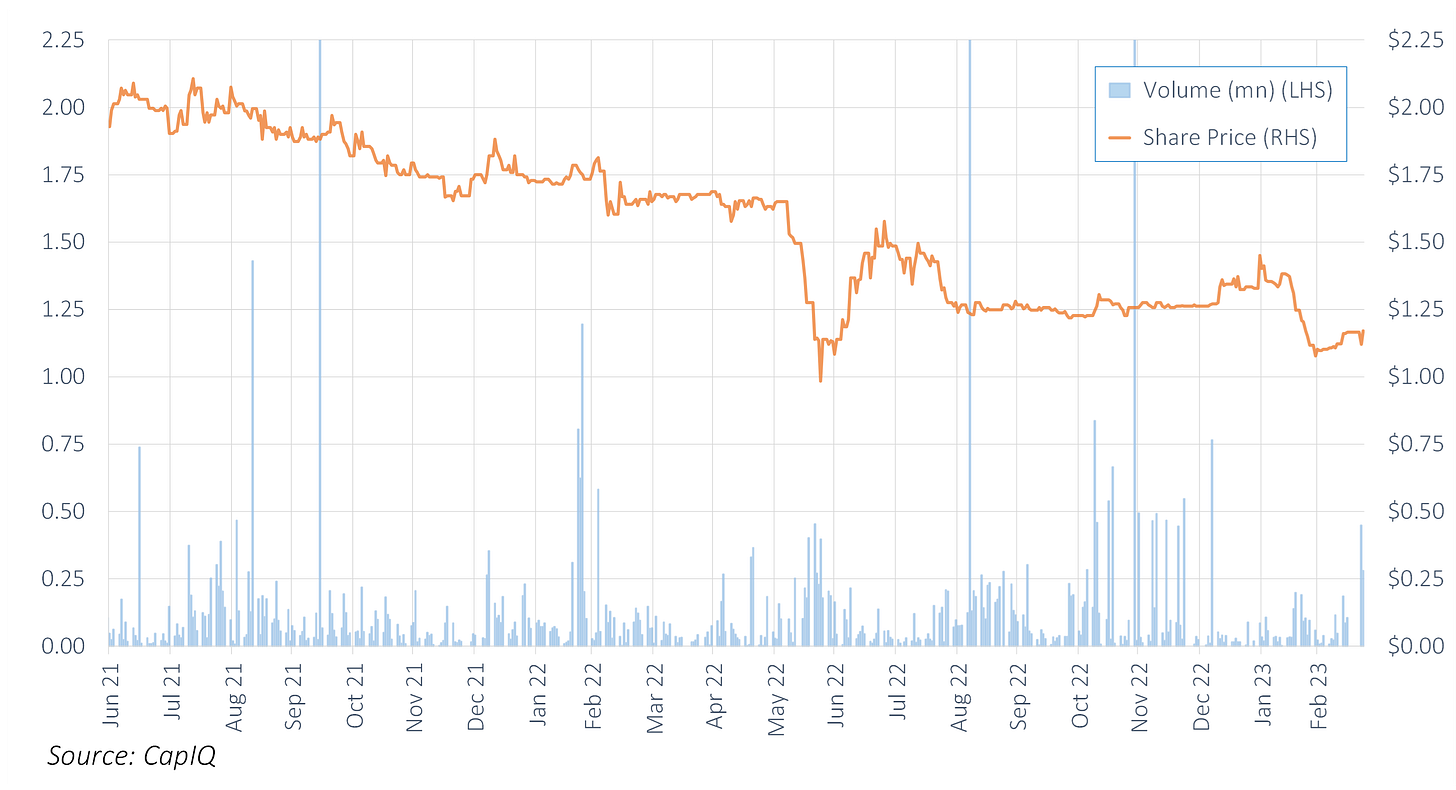
Price Performance
Latitude's share price has been trading down since listing.
Latitude has been one of the worst performers versus peers over the past year.
Conclusions
Unlike Medicare or Optus, Latitude is a financial services business. As such, there is a different level of trust expectation.
Latitude has been clear that this is not a Latitude system that was breached, but two separate service providers.
This may be moot, however, irrespective if this is part of the business that Latitude had no control over.
As a financial services licensee and credit provider, it still has a responsibility for that breach, and therefore is likely liable for that breach.
The chair of the Australian Computer Society Cyber Security Committee Louay Ghashash went on the attack, and described Latitude's inability to secure four separate access points as “ridiculous”.
Either this attack was so sophisticated that they compromised the multi-factor authentication of different service providers and Latitude itself, or there was a simpler explanation.
Latitude said it is not onboarding any new customers to its financial services.
This is not the time to enter here or on any further weakness.
Expect more granularity on the attack in the near future, which may further comprise/erode sentiment and confidence.
On the 27th March, Latitude said the cyberattack has ballooned to 7.9mn Australian and New Zealand driver licence numbers, the personal information of 6.5mn customers, and 53,000 passport numbers stolen - so far.